Identity theft, also known as identity fraud, refers to a crime in which somebody wrongfully obtains and and uses another person’s personal data to defraud, defame, or deceive, typically for financial or economic gain. It has become one of the largest and most problematic white-collar crimes today. According to Dan Ribacoff, “With the ease and accessibility of technology and platforms like the dark web, any document or transaction has the potential to be a scam. Identity thieves conduct identity fraud, both online and off, so you have to always be ready for them. To protect your personal privacy, adopt the same vigilance as you would to protect your home and valuables.”
The Different Kinds of Identity Theft
●Financial Identity Theft: This can occur when credit reports and bank accounts are breached. It is the type of identity theft that people are often most familiar with.
●Insurance Identity Theft: You may not realize it, but this illegal practice can yield big money for criminals. Medical care is one of the hottest commodities in the United States today.
●Medical Identity Theft: Scammers visit hospitals, emergency rooms, and pharmacies to receive medical care… and you’re actually the one paying for it.
●Social Security Identity Theft: Social Security Numbers can be sold to those who need US citizen statuses, such as illegal immigrants, along with driver’s license ID numbers.
●Income Tax Fraud: Scammers use your identity and file a false tax return, claiming a refund. They receive the refund, while you get stuck with an audit by the IRS. With e-filing, they can, while sitting around in their underwear, transfer the funds straight into a bank account, then withdraw the money and close the account… causing the trail to go cold for the authorities (but not for a private investigator).
#1: Beware of Dumpster Divers
You can tell a lot about someone just by seeing what they throw away. Garbage retrieval is one of the many ways that someone can get a hold of your stuff, but this method is actually legal. That’s why you need to trash your trash can!
Most people believe that only throwing out items with personal information like their name, address, date of birth, and Social Security Number is unsafe. However, any personal information is desirable to an identity thief. This includes documents that you may think nothing of, like correspondence from your child’s school, your spouse’s company, the stores that you shop at, your bank, etc. For example, if you receive a brochure from Bank of America, and a thief discovers it in your trash, he now knows where you bank and can try to deceive you:
“Hello, Mrs. Jones, my name is Sarah and, I’m calling from Bank of America to make sure that you received our flyer regarding your preferred customer status, dated March 24th. we are so thankful for your loyalty to Bank of America that we’d like to present you with an even better offer! Let me look up your account, so I can see the best interest rate that you qualify for. Would you please confirm the last 4 digits of your Social Security Number for me?”
Sounds pretty legitimate, right? The thief may already have the other digits of your Social Security Number, as they can be obtained by using commercially available databases and even some public records filings that just redact the last 4 digits. If they have that, all they have to do is connect the pieces of that number to become you on paper. The more believable a person sounds, the more likely you are to fill in the blanks for them.
In order to foil these dumpster divers, crosscut-shred, or confetti-shred, all personal documents. A crosscut shredder uses 2 contra-rotating drums to cut rectangular, parallelogram, or diamond shaped shreds, completely destroying documents so that not even Rain Man can reassemble them. Be sure to shred your personal documents and mail regularly, whether it’s when you’re watching TV or reading the Sunday paper. Make it part of your daily routine.
#2: Be Able to Spot Mail scams
You’ll find a lot of old-school conmen who still try to use snail mail to defraud someone. Here’s what they do:
● Issue fake checks and money orders.
● Offer fraudulent financial opportunities in the form of lottery and work from home scams.
● Offer fraudulent refunds from banks
As technology has gotten better over the years, so have mail scams! Publishing software applications like Adobe Photoshop allow scammers to effortlessly create posters, brochures, and flyers that look like the real deal. That’s why it’s so important to scrutinize all correspondence that you receive by mail. Always consider the following:
● Does this offer seem too good to be true?
● Is it poorly or unprofessionally written?
● Is the return address correct and complete?
● Is is addressed to you directly or to “Dear Resident” or “Dear Sir/Madam”?
● Does the company or organization even exist? (It’s as easy as a simple Google Search)
● Are greetings and closings correct? Does it say “Yours Sincerely”?
● Does it require you to send money or write a check? (Biggest red flag)
When in doubt, always contact the company directly. Also, to a Google Search to see where the company is headquartered, and contact the state’s secretary of state/division of corporations to make sure it is a legitimate entity.
#3: Look Over Your Shoulder
In addition to watching you at home, scammers will follow you around as you run errands or travel to and from work. Sometimes they can get close enough to glean credit card or bank card information. Once they get that, they’ll shoulder surf, or look over your shoulder as you punch in your pin or access code, or they’ll take a quick photo of your card with their phone as you slide it into the card reader. Shoulder surfing is most prevalent in crowded areas or close quarters where it’s easy to observe and not be noticed, such as the ATM vestibule of the bank. Make sure to always be aware of your surroundings when using credit/debit/bank cards and always cover the keypad when entering access codes.
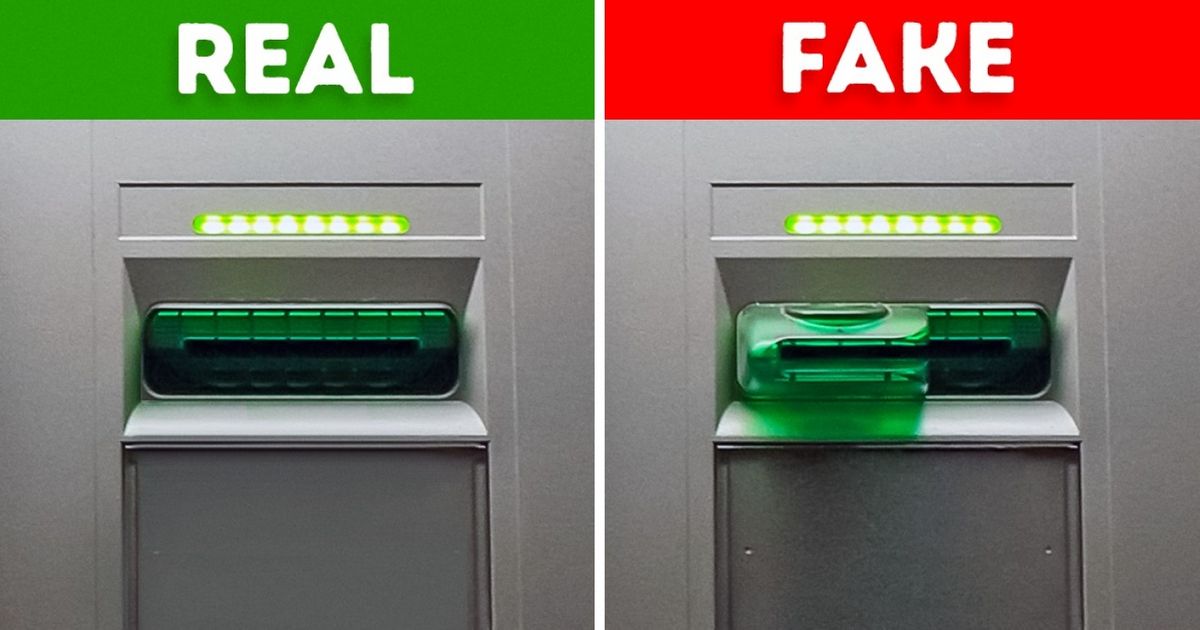
#4: Be Able to Identify ATM Skimmers
ATM skimmers are pretty easy to miss at first glance, which is why they are very much a threat to your personal information. Scammers will install hidden devices, called overlays, illegally on ATMs that enable them to view your account information from a nearby computer once you insert your card. It is very important that pay attention to the condition and design of any ATM that you use. An overlay can be inserted onto any type of unit that processes ATM, debit, or credit cards. The overlays are wafer thin and may not be noticeable unless you’re really looking for them.
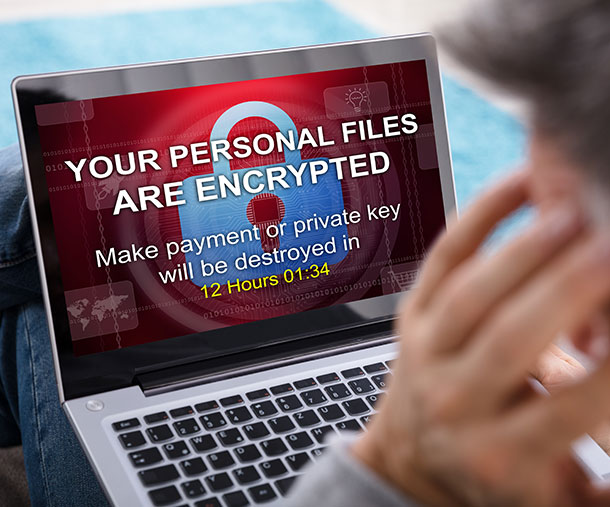
#5: Look Out for Monitoring Software on your Devices
Monitoring software, AKA computer surveillance software, allows for a hacker/scammer to observe and track your computer usage. As discussed in How to do Your Own Electronic Surveillance, it can be used for electronic surveillance legally if you install it on a computer that you own. However, many times these kinds of software are used for illegal purposes with malicious intent:
●Malware: Software that is used to damage or disable a computer. Computer viruses are the most common example of malware.
●Spyware: Software that allows hackers/scammers to monitor and steal your computer records and activities by transmitting all of your stored data onto their hard drive
●Key-logging: Software that records every keystroke (button-press) made on a computer. This allows hackers to gain access to passwords or other confidential information accessed on a computer.
The best way to protect yourself from these kinds of theft-programs is to utilize services of an identity theft protection company, such as LifeLock. Sure it’s a few extra bucks a month, but it’s a lot cheaper than dealing with the repercussions of getting your identity stolen. What each identity theft protection companies will do is safeguard your credit, financial data, and your good name. Utilizing a good antivirus program on your computer would also be a wise decision. I would recommend either McAfee or Norton, which will basically act as your computer’s virtual bodyguard. These antivirus programs will detect monitoring software or viruses found on websites that you visit. Don’t be cheap when it comes to protecting your devices, it’s very much worth it!
#6: Be Careful with Peer-To-Peer File Sharing
Peer-to-peer file sharing, or P2P for short, is a very popular way to share photos, videos, documents, etc. with others online. The way it works is you download software that connects your computer to other computers that use the same software, which could potentially connect you to millions of other computers at the same time (What could possibly go wrong?). Because you’ve now open up your computer to potentially millions of strangers, it puts your information at risk of being stolen or could allow others to give your computer some nasty (and expensive to fix) viruses. It’s very important to understand the P2P software that you may use and as said before, it’s always a good idea to install a reputable security and antivirus program (Think of it as a condom for your computer).
#7: Keep Safe of Phishing
For those who are unfamiliar with it, phishing is the act of attempting to acquire sensitive and personal information like usernames, passwords, credit card numbers, and Social Security numbers, by disguising oneself as a trustworthy entity via a website or email address. Think of an email sender line as you would Caller ID: it announces who is trying to contact you. Scammers will disguise themselves behind credible looking names or designations in order to gain access to your personal information. Like mail scams, phishing has become more and more sophisticated over the years. Here are some warning signs that something may not be what it seems to be:
●You are receiving customer notifications from a retailer or company, but you have never actually been a customer of that said company
●The email is not addressed to you. Instead, it is addressed to an unknown email address or undisclosed recipients
●There is an ominous warning of some kind. Some scary-sounding message, like “If you don’t respond to this email within 48 hours, we will shut down your account permanently!”
●Sloppy misspellings, improper punctuation, and awkward phrasing might be present in the message sent to you. Virtually no email sent to you has perfect grammar, but phishing scams often have more than their fair share of errors.
If you suspect that you have received a fraudulent electronic communication:
●Do not reply
●Do not click on any provided links from the sender
●Do not download or even click on any attachments
●Do not copy and paste any links into your browser
Instead, do contact the organization in a separate email, by phone, or through the official website and be very cautious of where you click.
#8: Listen closely for Vishing
Vishing, or voice phishing, is the attempt to acquire sensitive and personal information via voice calls made to a landline or mobile phone. Criminals go to great lengths to convince you that they are who they say they are in order to gain access to your private personal information. They’ll say something like, “I’m calling from your gas company and we want to update our client records. Can I just verify your social before we begin?”. A security-savvy person will never give our their personal information over the phone, especially when the person you are giving it to is the person who initiated the call and asked directly for it. Always remember that banks and credit-card companies already have your information; they will never call you and ask you to recite it for them. If you get a call that you suspect may be a vishing attempt:
●Tell the person that you will call them back, then call the 800 number on the back of your credit card, bill, or statement to report the call that you have received and verify that it was not actually them who called you.
●As a test, offer a fake account number. If the person says “Yep, that’s correct. You’re in”, hang up and call the authorities immediately.
#9: A Word on Passwords
Passwords are one of the most secure and important lines of defense against identity theft. Every account that you have should require a password for access. That includes cell phones, banks, email addresses, credit cards, etc. It’s an extra layer of protection beyond those security questions that ask things like the name of your first pet or your father’s middle name.
When selecting a password, too many people make the mistake of choosing something personal—the name of their dog or child—because it’s easy to remember. The problem is that it’s also easy for a scammer to figure out. All they have to do is look you up on social media, find a picture of your dog, zoom in on the tag of its collar, and BOOM, they’ve got access to all of your accounts. Do you know how many people know of my dog, Harley? There might be more pictures of Harley than Kim Kardashian on the internet. If I make “Harley” my password, I may as well write out a blank check for a scammer. Some password tips:
●Make your password ridiculously stupid: FrenchToastAndKetchup1985 or MyBananaOpenApplesauce2000. Who in the world is going to think of that?
●Don’t even use real words: Try something like blickypuckanow.
●Store passwords where people cannot gain access to them: There are free apps out there called password keepers that protect your password information for you and require face/fingerprint identification to access the app. They are a lot safer than just writing it down on a piece of paper.
●Change your password regularly: People get too complacent and may have the same password for the last 30 years. However, it’s a good idea to change your password every 6-12 months. If you think there’s been a breach of any kind or you’ve clicked on a sketchy link, run a virus scan on that device and then change your password on another device incase there’s been any spyware installed on the original device.
#10: Keep your Wits when Shopping Online
There’s no denying the ease and convenience of online shopping. Who wants to go out to the store in the cold rain or snow to buy a Valentine’s Day gift when all you have to do is click a few buttons on your computer or smartphone? However, online shopping has its hazards and cautions, so it’s important to shop smart—this means not only knowing the best sites to to buy shoes on, but also how to avoid the perils of identity theft:
●Make sure the retail stores that you shop with are legitimate. Always manually type in URLs and email addresses
●Use your credit card rather than your debit card. Credit cards will protect you against fraud, while with debit cards, it’s way more difficult to recover lost funds.
●When reviewing items on credit card bills, look for small purchases—$1 here, $2 there. Thieves will test a stolen credit card with a few small purchases first to make sure that the number is good.
●Use things like Apple Pay, Google Wallet, or similar mobile-payment software. There is much less risk of other people getting your information when all you do is click a button, rather than entering in all of your information manually. By doing this, you completely eliminate the risk of spyware (It can’t track your keystrokes if you don’t type anything). You will also receive a notification every time you make a payment, so you’ll be immediately notified for any fraudulent payments.
Final Thoughts
Unfortunately, even with all the best-laid security protocols, your personal information may still be at risk if there is a date breach at any of the the businesses that you do business with. Scammers will find vulnerability wherever they can. The best thing you can do is take care of your end. Educate yourself, Install protective services. Be mentally prepared. As a private investigator, I use ruses all the time to extract information from targets of my investigations (See how I conduct Physical Surveillance and Electronic Surveillance). Don’t fall for people like me.
